One of the company's websites has been defaced, raising alarms. Collaborate with other analysts to uncover the identity of the adversary and assess the situation.
Threat Intelligence Tags: exiftool, officemalscanner, CyberChef
Scenario Haunted Company Inc., a long-established Credit Reporting Agency, has been successfully operating in major financial hubs such as New York, London, and Tokyo. As a privately owned entity without external investors, the company has maintained consistent client satisfaction and steady earnings reports. With plans for expansion, the management has decided to take the company public, and the Initial Public Offering (IPO) is scheduled to occur within the next few days.
However, a crisis emerged just as the IPO date approaches. One of the company's websites has been defaced, raising alarms. Shortly after, it is discovered that the company's Tokyo server has come under attack. Concerned about the timing and the potential damage to the company’s reputation, the management is determined to identify the threat actor behind this attack and understand the breach mechanism to create detection before the IPO.
As a Threat Intelligence Analyst, you are tasked with collaborating with other analysts to uncover the identity of the adversary and assess the situation.
Available External and Internal Threat Intelligence:
New York(External: Business Commonality): Report on the 2017 GenX Breach, a major cyber attack on a leading Credit Reporting Agency. London(Internal Intelligence: Adversary Analysis): Analysis report for Haunted Company Inc., including Asset-Threat Mapping and adversary analysis featuring FIN7, APT27, Twisted Spider, and TG-3390, all of which are known to target the finance sector. Tokyo(Cyber Activity Attribution): Malware analysis from the compromised server, providing critical insights into the tools used during the attack.

After deployed an investigation machine, we will see "Investigation" folder on the desktop that stores files and tools that will be used for our investigation and it seem like we got 2 text files to read then lets start with README.txt first.
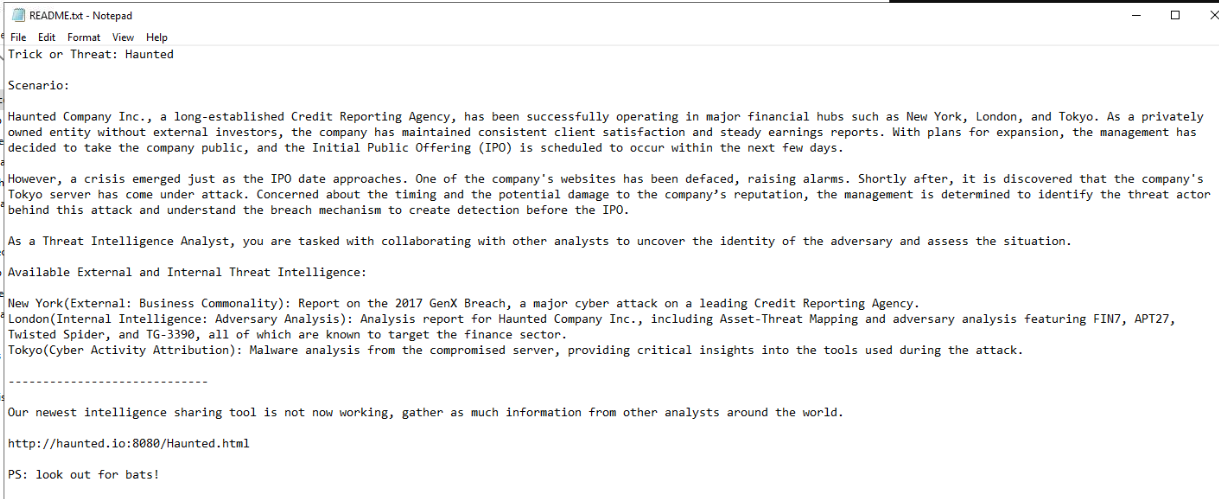
Then we will be presented with the scenario and a link to html page.
DecodeME.txt file contains base64 strings and before we decode it, lets access link provided in README.txt first.
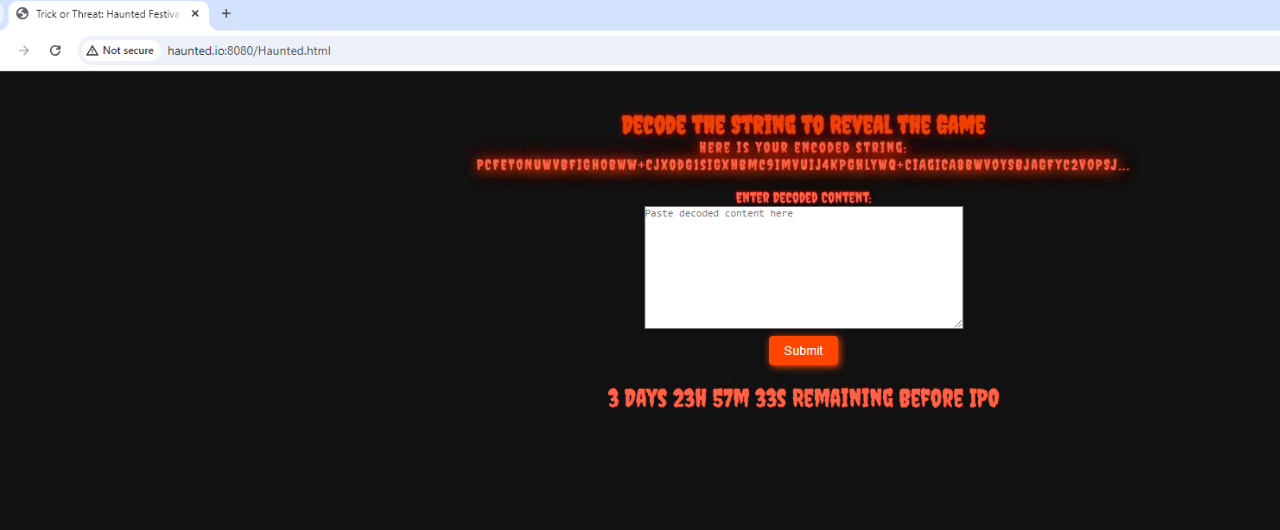
So we have to decode base64 and put it in this box and submit it.
Upon decoding base64 strings, we see that its a HTML code so I guess we have to submit it to combine 2 HTML code from website and this decode HTML code together to make it functional.
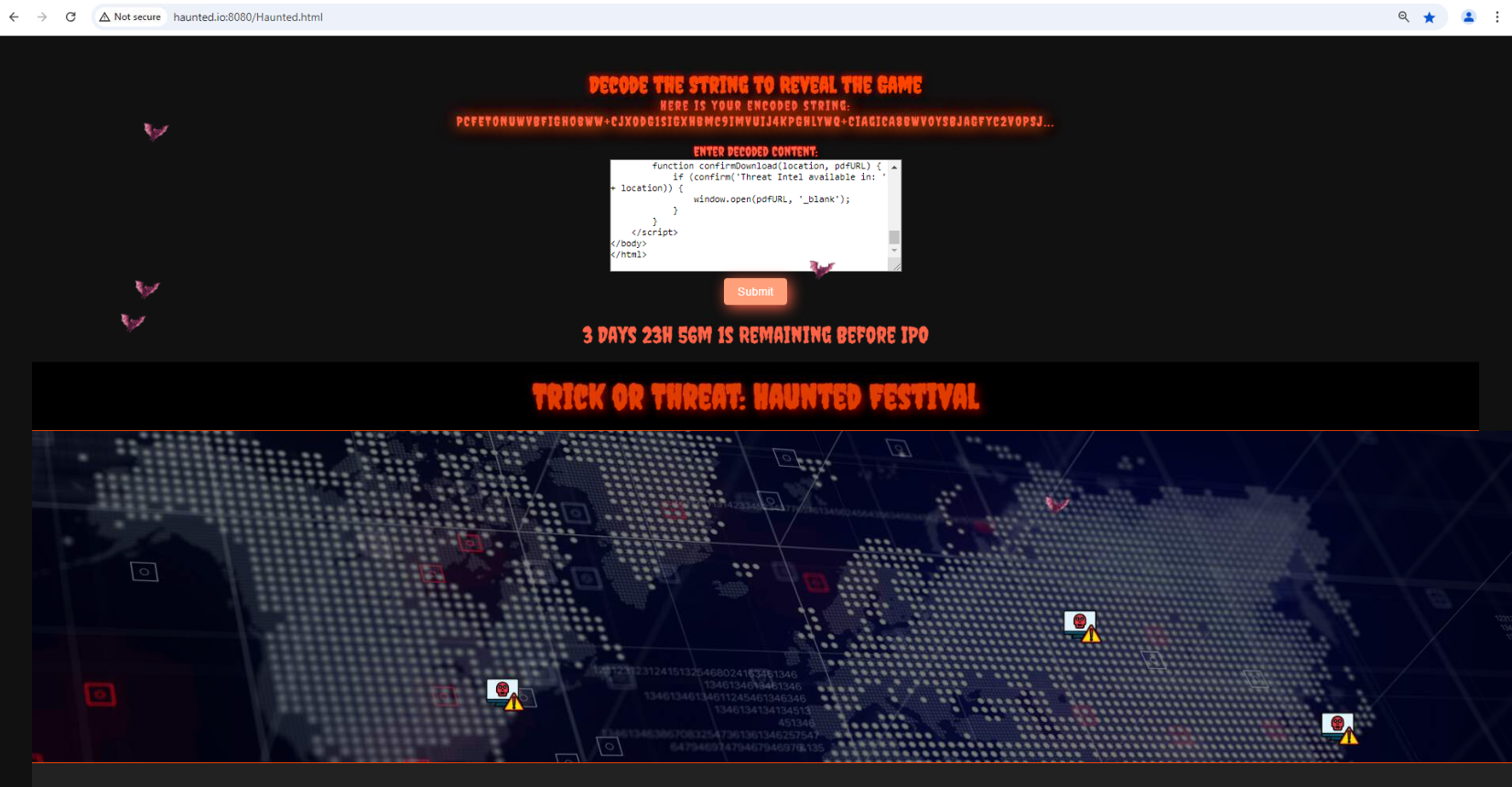
After submit it, threat intel feed will be displayed and we will see a lot of bat flying around along with 3 markers displayed on the map waiting to be clicked (And this site became so laggy after we rendered them.)
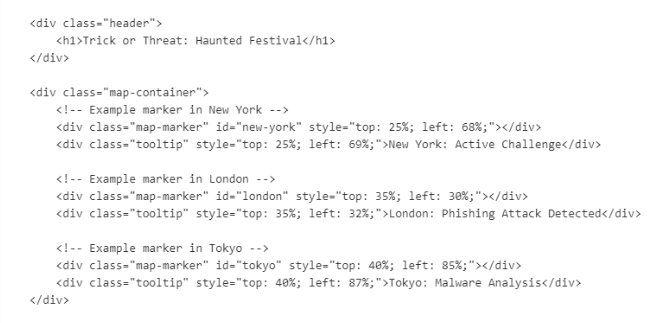
Without a choice, I have to read HTML code we just decoded then I found that those 3 markers represented New York, London and Tokyo threat intel.
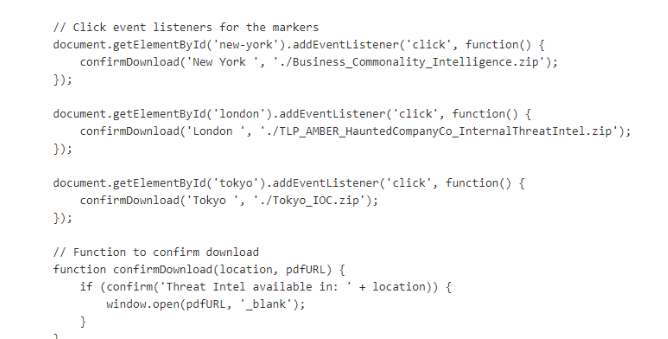
Scroll down for a bit which we can see that after we click those markers, we will download these 3 files so lets download them all.
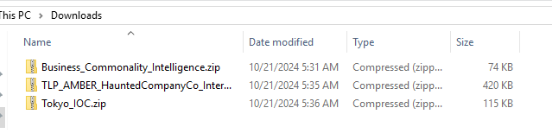
Now lets extract all the files to it respective folders.
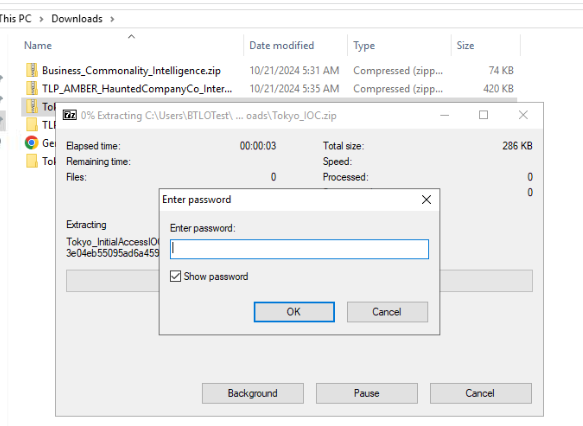
We can extract 2 files but only Tokyo IOC is password protected so we will have to figure it out somehow.
Q1) In 2017, a well-known company was attacked. What is the name of the company, its country of origin, and its business model? (Format: XxxX Xxxxxxxxx, XX, Xxxxx Xxxxxxxxx Xxxxxx)
We know that London has report on the 2017 GenX breach which might related to this question so lets open it.
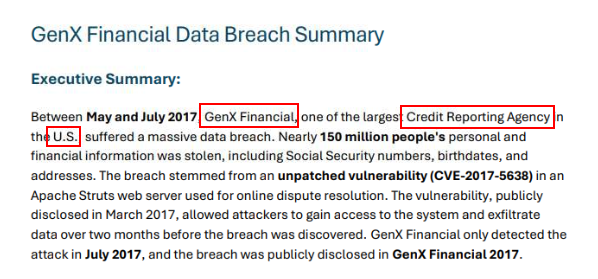
Then we could see the name of this company, its country and business model right here.
Answer
GenX Financial, US, Credit Reporting AgencyQ2) According to the data breach summary, one of their critical assets was compromised, and they later discovered a vulnerability in one of their public-facing applications. What type of weakness was exploited to breach their network? (Format: Axxxxxxxxxx Vxxxxxxxxxxxxx)
Then after reading through this report, you might notice this breach was caused by unpatched vulnerability specifically for CVE-2017-5638
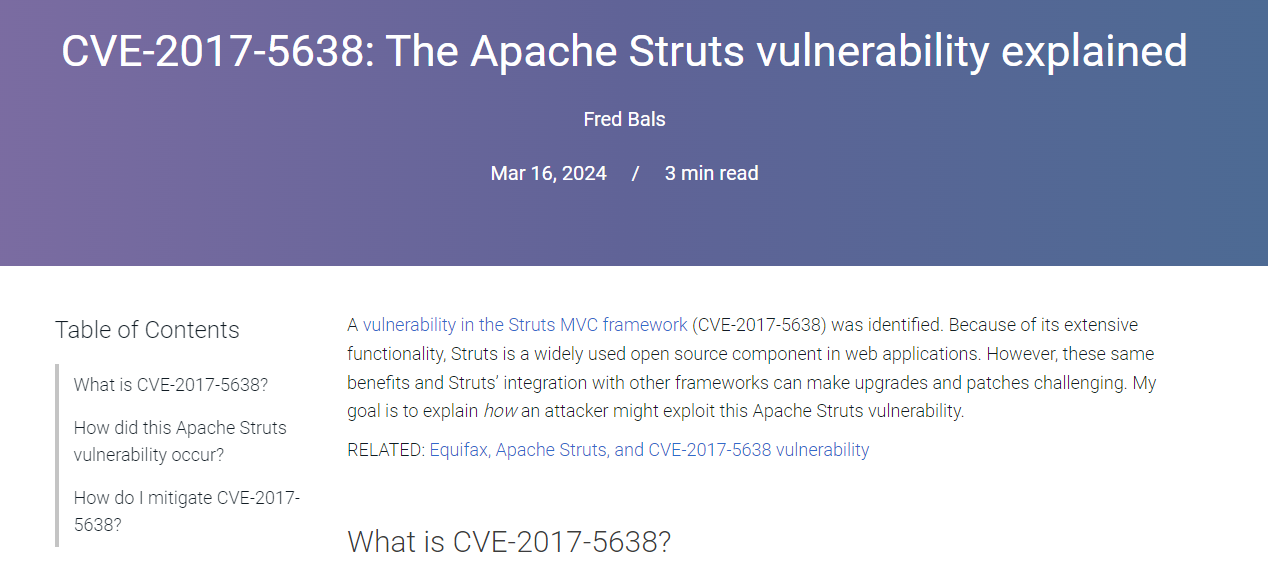
Which is Apache Struts vulnerability which is an "application vulnerability" that lead to remote command injection attack or RCE.
Answer
Application VulnerabilityQ3) How long did this breach go undetected? What was the Mean Time to Detect (MTTD)? (Format: XX days)
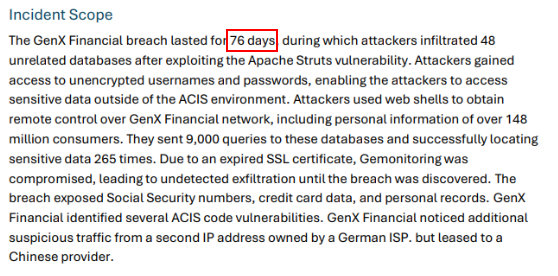
You can get an answer of this question right here.
Answer
76 daysQ4) What application was targeted by the attacker? What vulnerability was exploited, and where is this application located within the network? (Format: Xxxxxx Xxxxxx, CVE-XXXX-XXXX, XXXX)
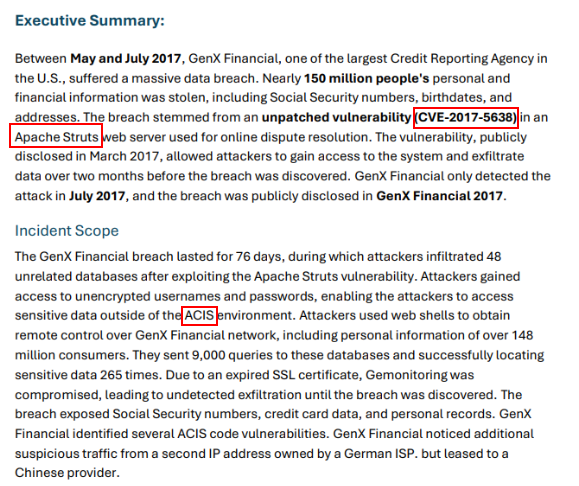
We already know that its CVE-2017-5638 of Apache Structs but which system was affected? after reading Incident Scope then we can see its in ACIS environment.
Answer
Apache Struts, CVE-2017-5638, ACISQ5) The attackers exfiltrated millions of records. How many consumer details were estimated to be exposed, and how was this data left from the premises and through which channel was the data exfiltrated? (Format: XXX Million, xxxxxxxxx)
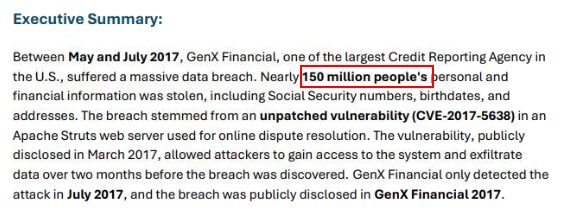
Approximate number of personal and financial information that was stolen is around 150 million right here.
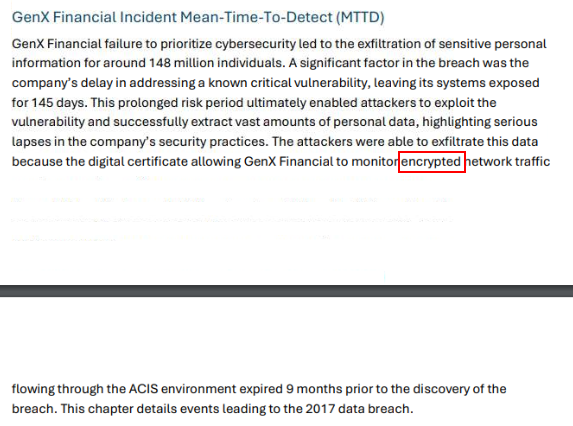
And because of digital certificate, it allowed the attackers to exfiltrate data via encrypted network traffic.
Answer
150 Million, encryptedQ6) Later, during the investigation, a flaw was discovered in their ACIS code rendering system. What were these flaws? (Format: XXX Xxxxxxxxx, Xxxxxxxx Xxxxxx Xxxxxx Xxxxxxxxx)
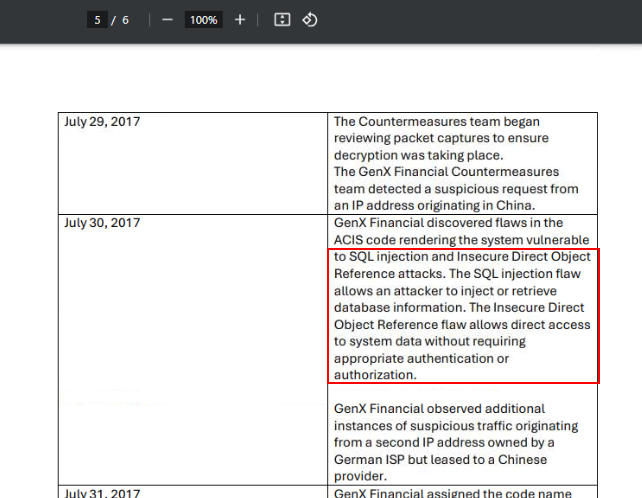
From Incident Scope, it was mentioned that ACIS code has several vulnerabilities and that include IDOR and SQL Injection.
Answer
SQL injection, Insecure Direct Object ReferenceQ7) What file was inserted during the attack, and which country did the attack originate from? (Format: XXX, Xxxxx)
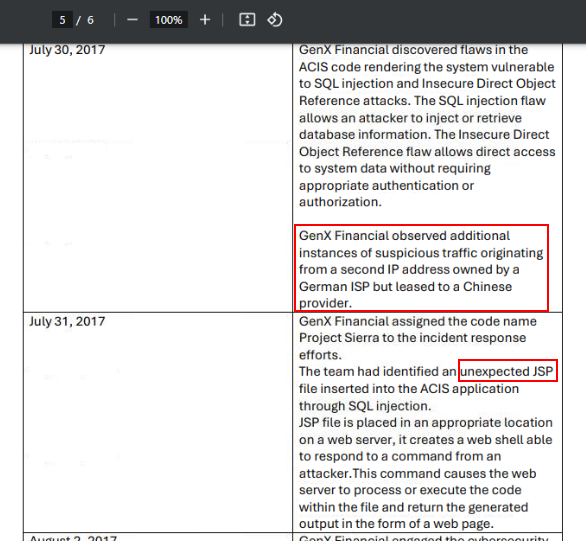
GenX observed that a suspicious IP address owned by a German ISP but leased to a Chinese provider so the country is China and the file inserted during the attack is JSP file which exploited SQL injection attack to deliver it.
Answer
jsp, chinaQ8) It is said that if a specific network security technique had been properly implemented, the attacker likely would have failed to accomplish their mission. What is this technique called? (Format: Nxxxxxx Sxxxxxxxxxxx)
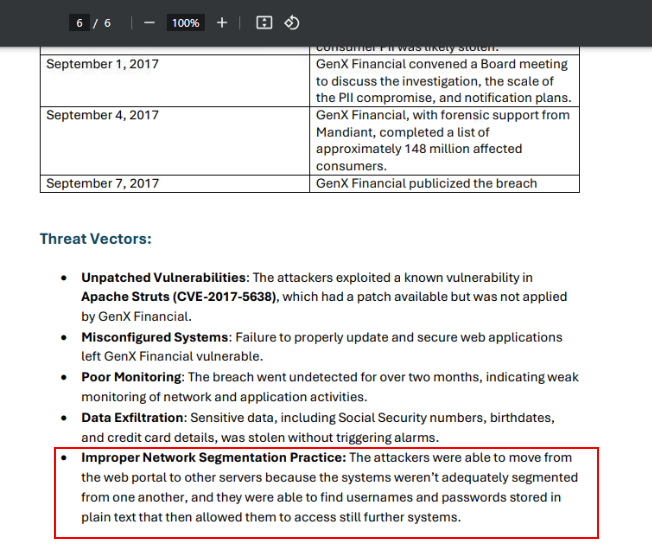
Go to Threat Vectors section which we can see that this company did not implement network segmentation which can reduce scope of the breach and limited what the attackers could do in a single network segment.
Answer
network segmentationQ9) Adversary Analysis, this one group in particular as being involved in numerous attacks, including an attack on a medical research company during COVID-19. What is the name of this threat group (according to MITRE), what threat vector do they use, what is their country of origin, and what is their motivation? (Format: XXXX, Xxxxxxxxxx, Xxxxxx, Xxxxxxxxx)
Lets learn more about 2 adversaries provided by this investigation.
First adversary that we are going to learn is FIN7
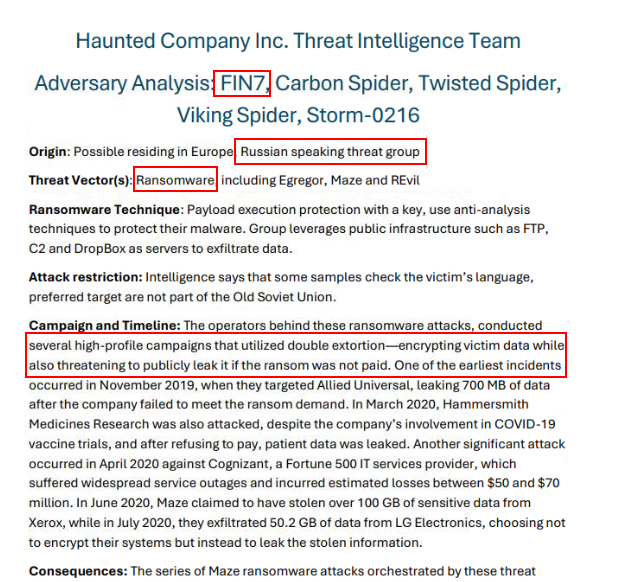
Which is Russia speaking threat group that mean they must originated from Russia and they used ransomware to conduct several high-profile campaigns and also utilized double extortion technique that will ask for more money to not exposed private files to public so their motive is financial gain.
Answer
FIN7, Ransomware, Russia, FinancialQ10) Investigating the other threat group. What is the APT number assigned to this group? What is the name of the specific operation that involved dropping web shells on SharePoint servers? In what year was this group first observed, and what is their possible motivation? (Format: APTXX, XxxxxXxxxx Xxxxxx Xxxxxxxxxx, XXXX, Xxxxxxxxx)
Lets take a look APT27 this time.
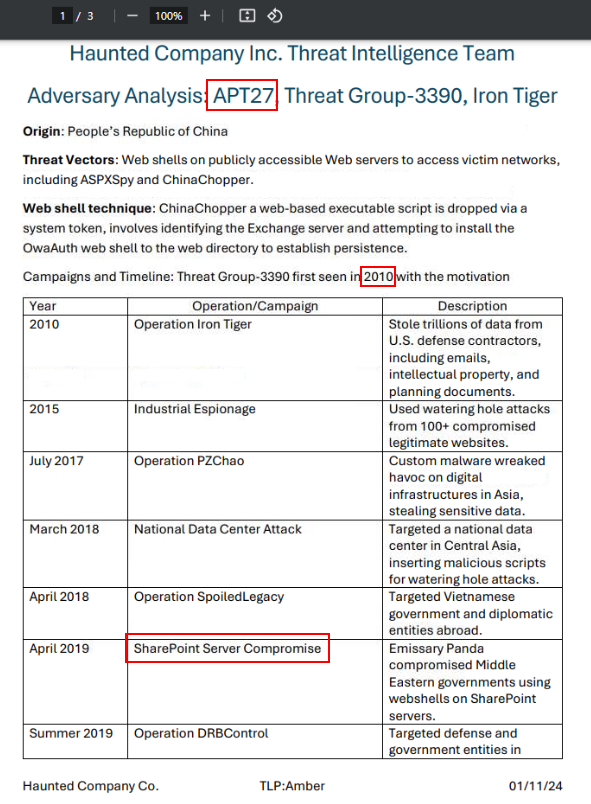
Then we can see that this group was first seen in 2020 and their campaigns aimed to stole sensitive data including Intellectual property and other important documents which make their motive "espionage" and the operation that involved dropping web shells on SharePoint servers is SharePoint Server Compromise.
Answer
APT27, SharePoint Server Compromise, 2010, espionageQ11) Haunted Company Inc. in Tokyo is under cyber attack. Based on the IOCs that were provided (hint: BAT!), what attack vectors did the threat actor use? (Format: Sxxxxx Exxxxxxxxxx, Wxxxxxxx)
Its time to find Tokyo IOC zip password, lets take a look at what we have
- "Look out for bats!" from README.txt
- exiftool provided
So I guessed that we will get more file from clicking those bats.
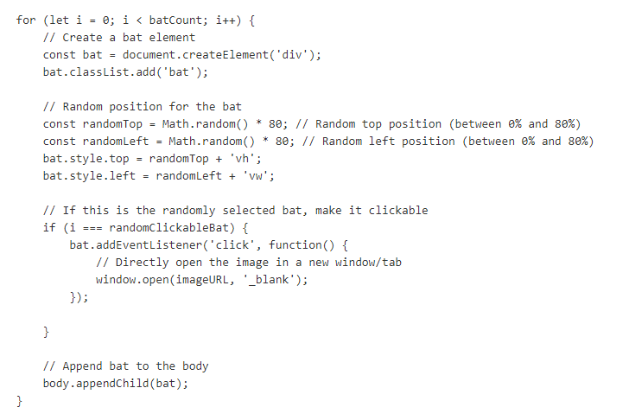
So I read HTML code from base64 decode again then which I can see that these bats have eventListener waiting to be clicked.
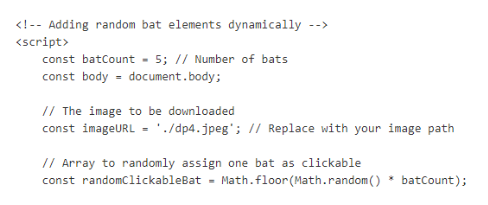
And if we clicked 5 of them, new image will be displayed
This is an image to download.
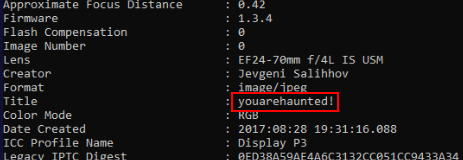
Then we can see Title metadata of this image does look like a password but it couldn't be used to unzip Tokyo_IOC.zip
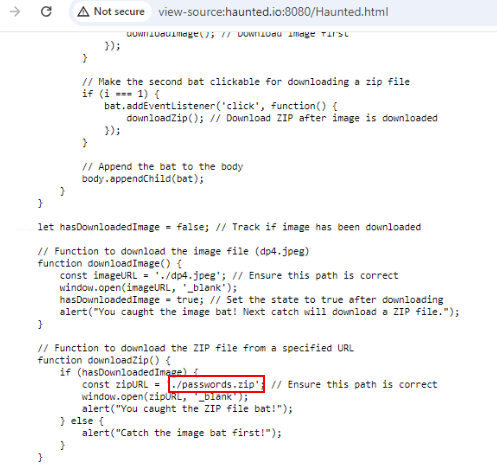
So this time I had to inspect page source which revealed everything about this page including this file that will be downloaded if image has been downloaded via legitimate way (clicking those annoying bats)
Well since we already know a path then we can download it then use password obtained via exiftool to extract file inside of it.
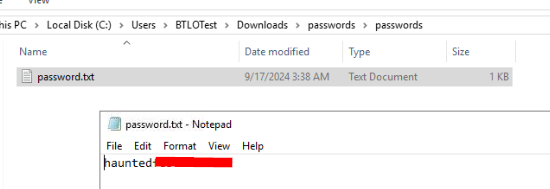
Which is a password that can extract Tokyo_IOC.zip.
Now we have 2 files from these 2 folders left to be analyzed.
First file is Rich Text Format (rtf) file which was created by Microsoft Word and known for being abused to embedded malware and the way we could deliver this is to use something like "phishing" or "social engineering"
This one is aspx file which is a "webshell".
Answer
social engineering, webshell
Q12) One of the IOCs contains shellcode. Use a tool and review the output to identify the offset of the PEB (Process Environment Block). (Hint: Output + OSINT!) (Format: 0x..)
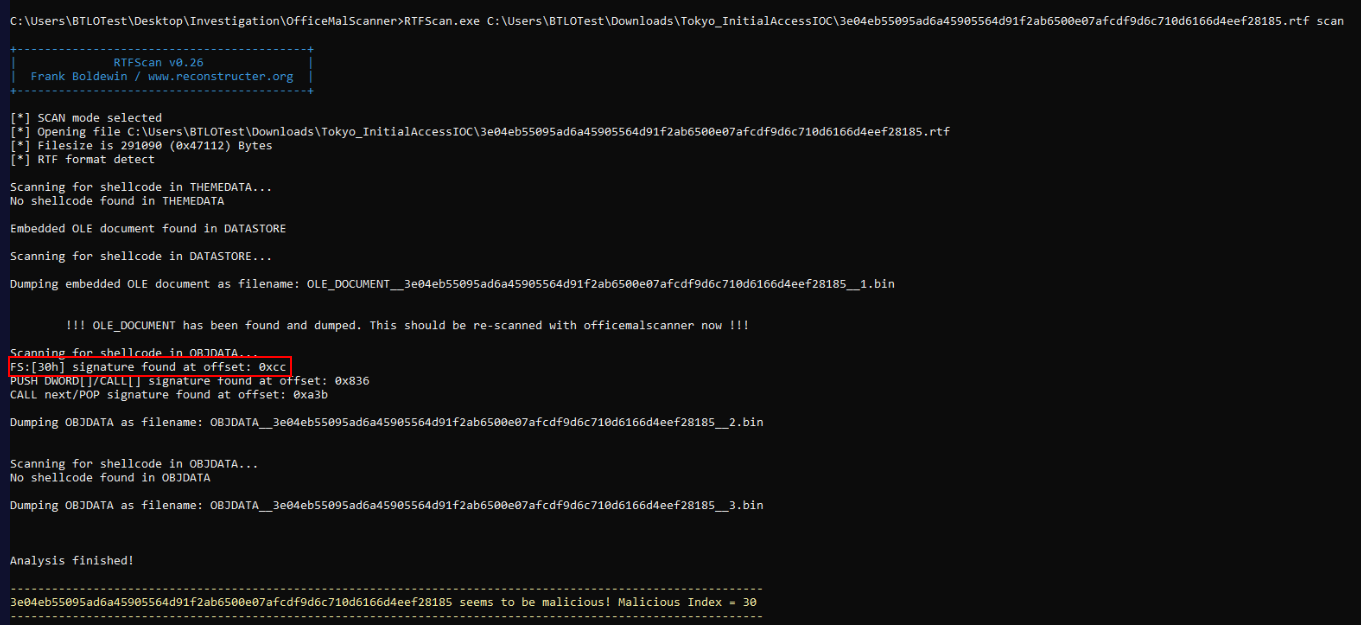
For those who do not know what PEB is and why we have to find it, PEB holds information about the process's execution and it also provides direct, low-level access to crucial information about the process without needing to call higher-level API functions, which could be monitored or intercepted by security tools and since we have OfficeMalScanner which also comes with RTFScan so we will have to use it to retrieve offset of the PEB like this.
Answer
0xccQ13) Based on the intelligence gathered, which threat group was responsible for the cyberattack on Haunted Company Inc.? What is the name of the malware they used to compromise Tokyo's infrastructure? (Hint: OSINT!) (Format: Xxxxxx Xxxxx-XXXX, XxxxxXxxxxxx)
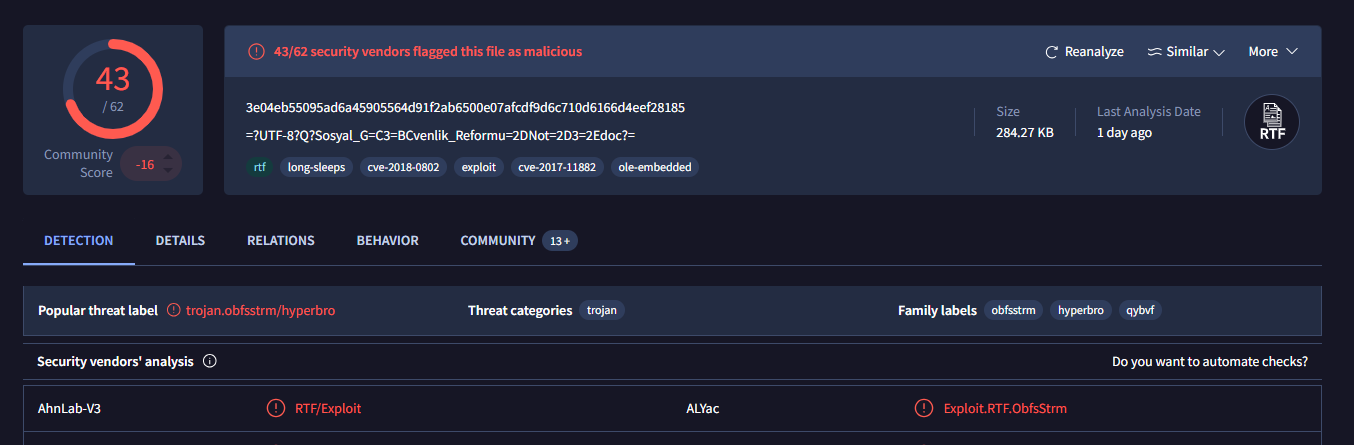
First, I searched rtf file hash on VirusTotal which reveals CVE related to this exploit and we can also see that there are a lot of community comments about this file.
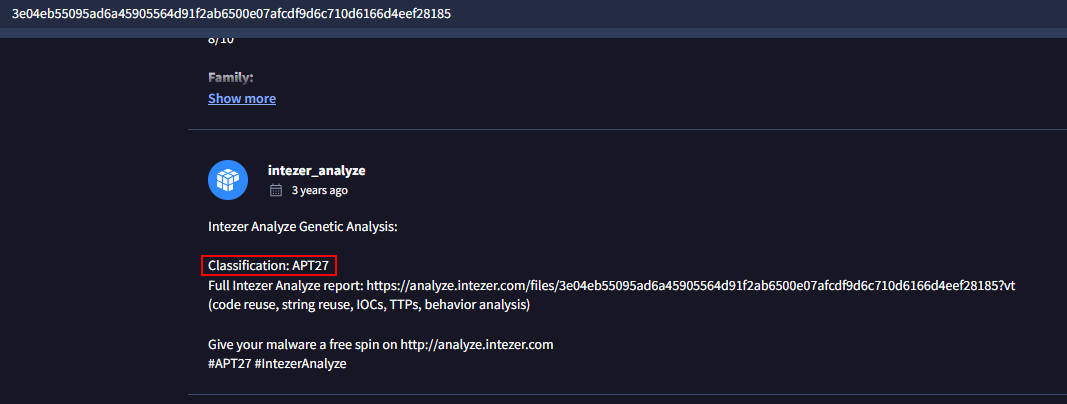
Then we can see that this file is used by APT27.
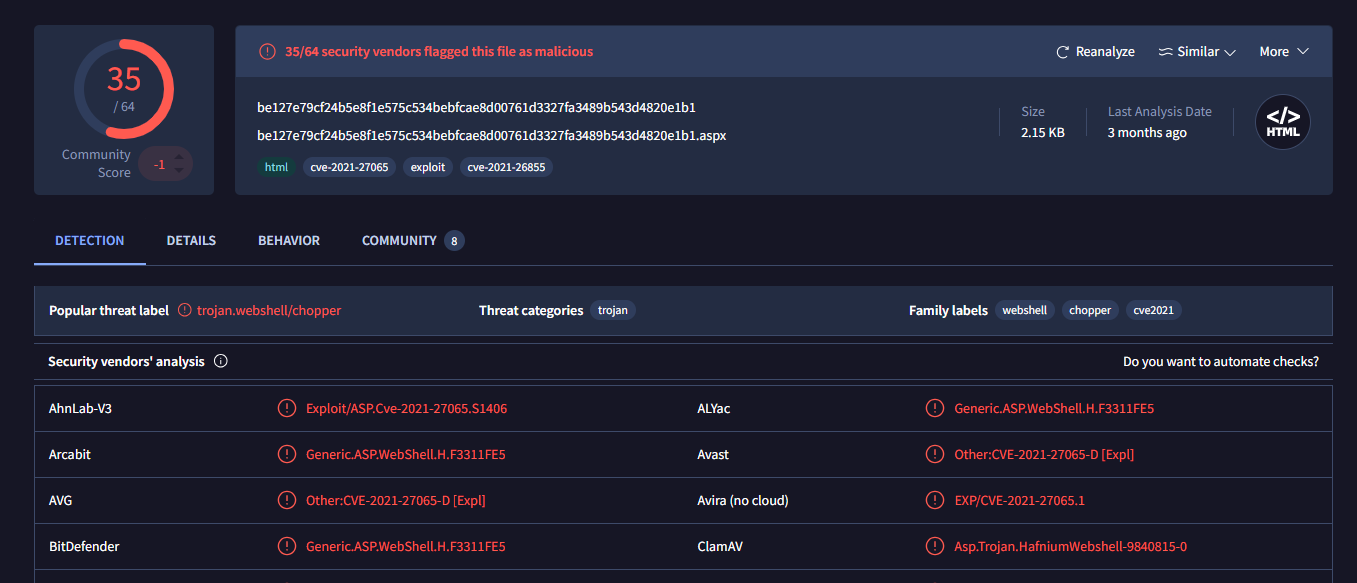
And the webshell is also known as ChinaChopper.
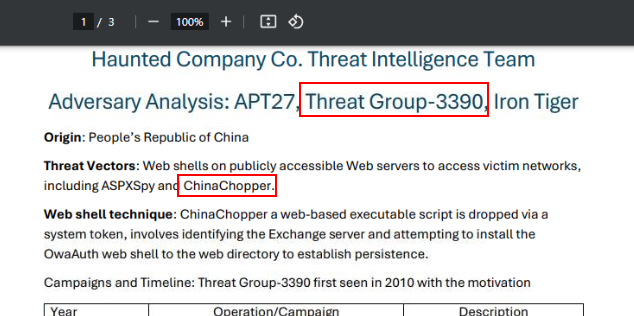
Remember Adversary Analysis? APT27 also known as Threat-Group-3390 which used ChinaChopper (aspx file / webshell we found) as their tool.
Answer
Threat Group-3390, ChinaChopperQ14) It seems the attacker leveraged a weakness in Tokyo's infrastructure. What is the latest CVE for this version that the threat actor exploited, and what type of attack was it? (Format: CVE-XXXX-XXXXX, XXX)
For this one, we have to take a look at this company's assets to find out which asset exposed to which latest CVE and it might has to be RCE one.
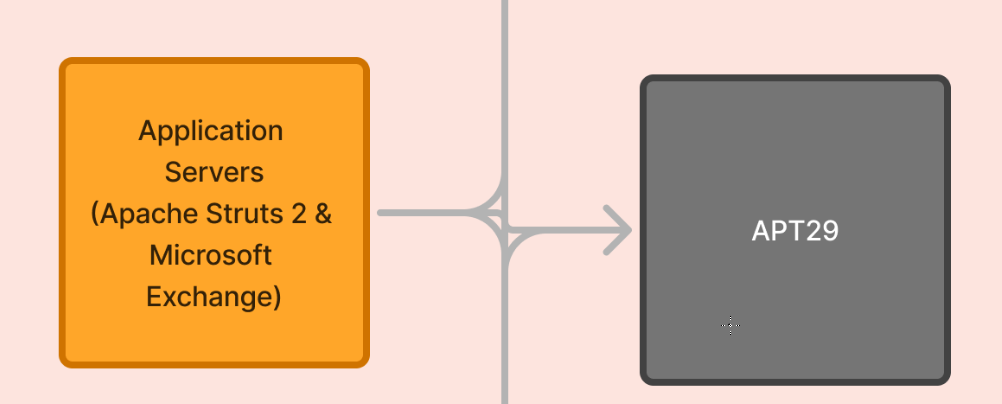
Then we can see that we have Apache Struts 2 and Microsoft Exchange for Application Servers.
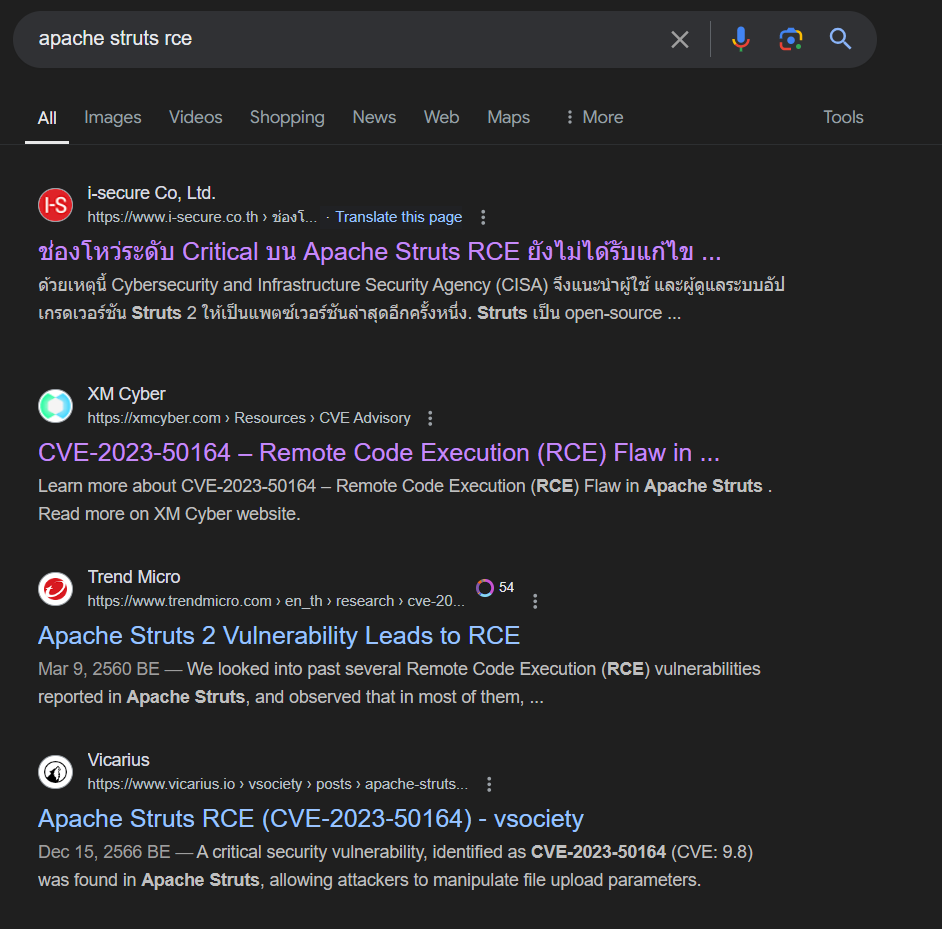
Then we will see another Apache Struts 2 CVE for RCE discovered on 2023 that is the answer of this question.
Answer
CVE-2023-50164, RCE https://blueteamlabs.online/achievement/share/52929/242
https://blueteamlabs.online/achievement/share/52929/242